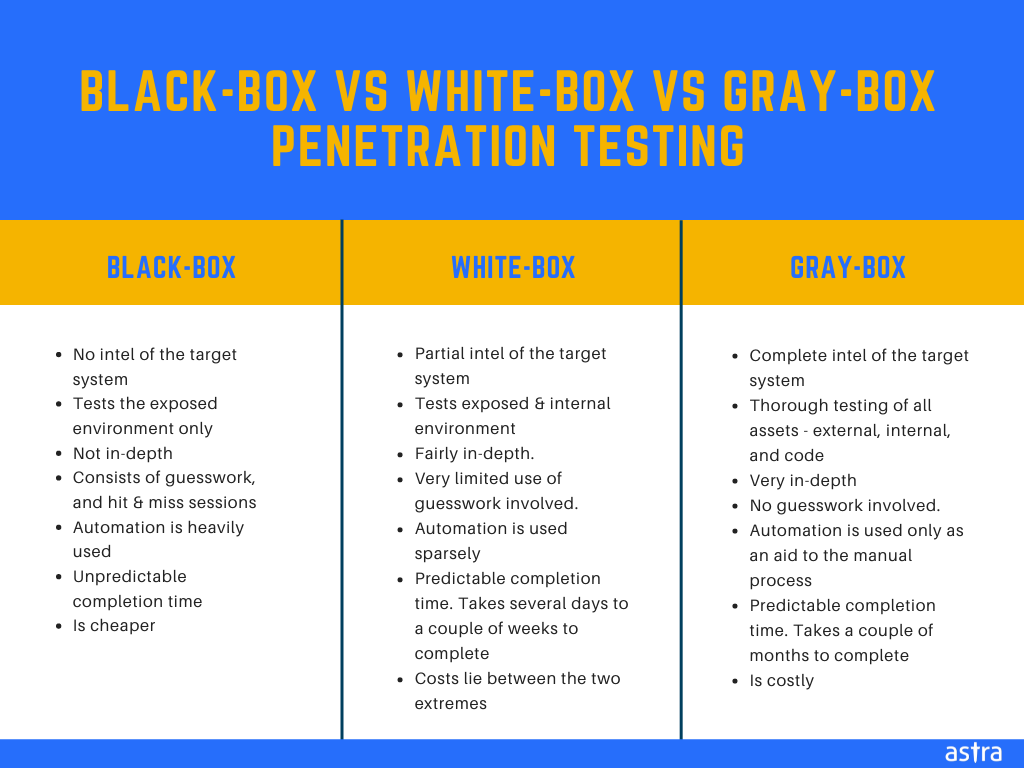
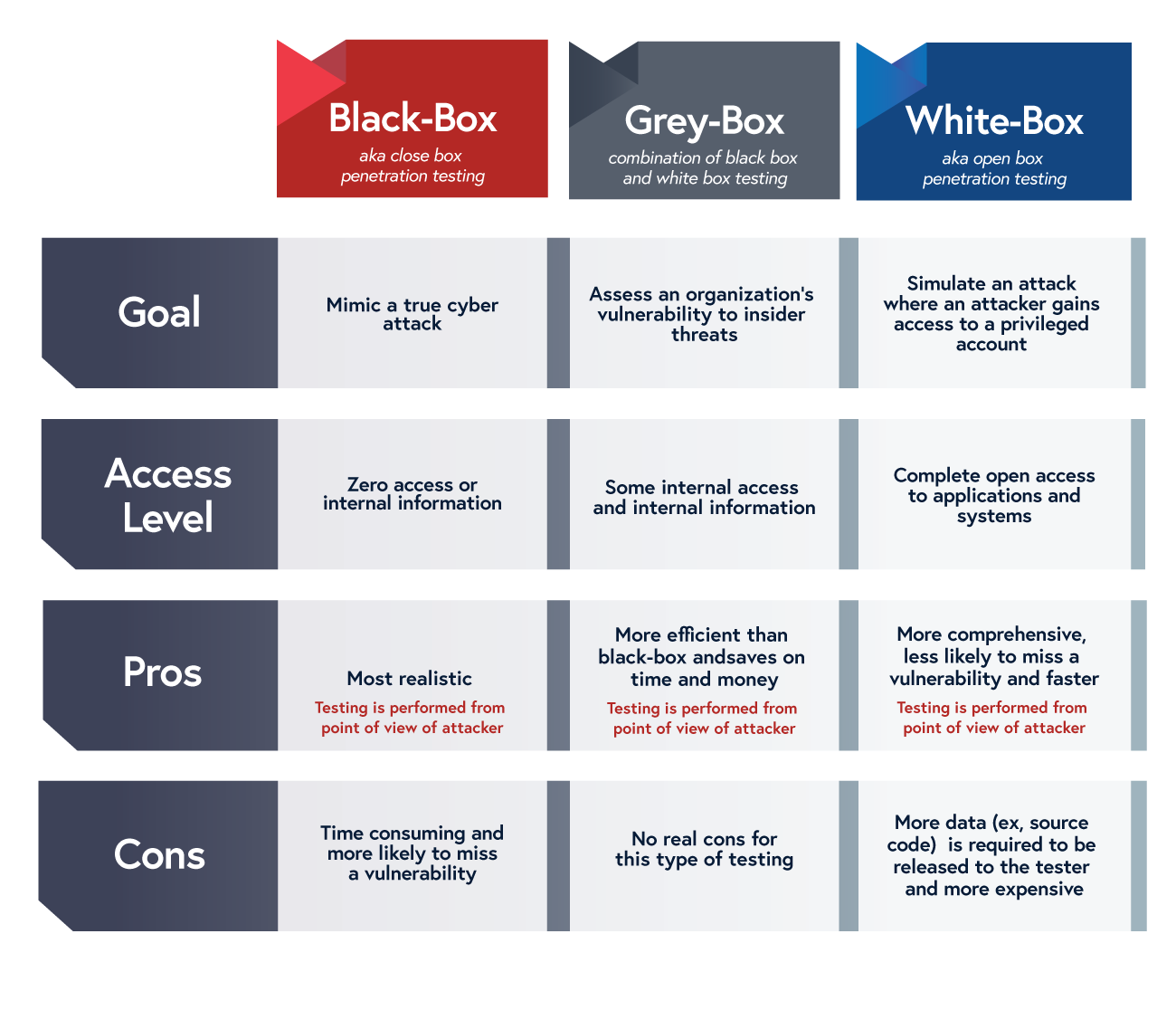
Penetrating the black box, hacking as an emancipatory strategy in Art, Science & Technology – Workshop with Patrícia J. Reis – Mz* Baltazar's Lab

A little black box makes it easy to unlock almost any iPhone even when it's secured with your fingerprint | Business Insider India